Part 2: IT RAR - Risk Treatment v2


RAR 2-1: Risk Treatment and Evaluation of Existing Controls
Note that the text in italics serves as supporting instructions for participants attending and attempting BCM Institute's Blended Learning assignment
After identifying the list of threats faced by the organisation in the previous section, participants will then proceed to the Risk Treatment and Control section
Threat (Col 2)
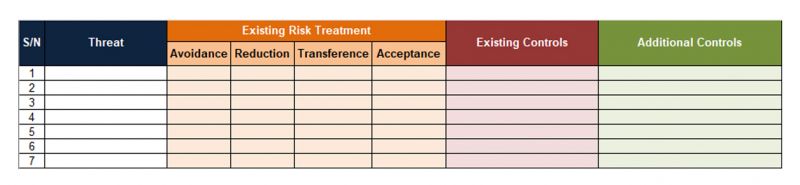
The name of each threat identified in List of Threats.

- Organisation BCM Coordinators are to ensure that all threats that have been highlighted in the previous section are represented here under the threat column.
Existing Risk Treatment (Col 3 to 6)
Existing Risk Treatment refers to the mitigating measures already put into place by the organization to handle recognized threats. 4 risk treatments are available to address the majority of the risks posed by threats
Read more explanatory notes for Risk Treatment. Note that the assignment of Risk Treatment is based on the overall risk appetite of the organisation’s top management, which may vary from a different organisation.
Existing Controls (Col 7)
These are the controls currently implemented for the organization to mitigate the risk posed by the threat.
- Controls are instruments or practices that are used to manage risk. All controls fall within one of the above 4 treatment options and serve as an elaboration of the existing risk treatments.
- Existing Controls are "Controls" that are already implemented within your organization to manage the identified risk.
- For example, if the fire is a threat, existing controls could include fire extinguishers, fire wardens, and an evacuation plan.
Additional (Planned) Controls (Col 8)

- Additional "Planned" Controls are Controls that will be identified within the questionnaire.
- In the example of fire again, an additional control could include setting up an alternate assembly area to congregate in the event of wet weather
Instruction to BL-DR-3/5 M2 Participant
- Select at least two (2) threats from IT RAR 1-1 List of Threats.
- Complete every entry for all the columns for the two threats.
- Remember to highlight the existing control if you have selected and inserted "Y" in one of the four "Risk Treatment" entries.
- It is alright to have more than one risk treatment for each selected threat
- Do remember to propose "Additional (Planned) Controls" that you may want to recommend to your organisation.
