Conduit Devices
1. Similar to the human element, conduit devices within the organization play a significant role due to the data it produces or utilises. These devices are either used as an intermediary to proceed with the attack or attacked to take over their Command and Control capabilities.
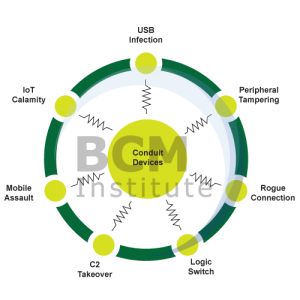 Examples of conduit devices cyber security threats:

|

2. Devices play a significant role in data breaches as assets targeted either for the data they store/process or because of their accessibility to the outside world. We often see devices used as tools to advance an attack, as well as device ownership and management often appearing as a factor in data breaches.
Source: (Verizon, 2016)
3. As with humans, devices also play a substantial role in data breaches. Vulnerable devices can be targeted because of the data they store or process and are often used by threat actors as Command and Control (C2) platforms or pass-through intermediaries. Conduit devices consist of networking equipment, servers, desktops, laptops, tablets, smartphones and portable storage devices. This represents an unending list of devices to protect and monitor.
Source: (Verizon, 2017)